I work at Seven West Media here in Perth on a small ops team. One part of our job is managing about one hundred EC2 instances in AWS. About half of them are on our SOE and the other half are a mixed bag.
The recommended best practice for administering a fleet of Linux servers is to set up a ‘jump box’ server which has no other purpose but to allow you to connect by SSH to the rest. This special server is also sometimes called the ‘bastion host’.
The basic idea is that if you allow access through only one point then it should be easier to control and audit. The flip side is that you now have a single point of failure – you have put all your eggs in one basket.
… in the increasingly popular world of DevOps, having a one-off solution that generally needs to be manually controlled and updated is heading in the opposite direction of consistency and automation.
Rajat Bhargava
http://radar.oreilly.com/2014/01/is-the-jump-box-obsolete.html
I tend to think that a well-managed firewall is probably sufficient but it is actually not that simple. You see a jump box also allows you to connect to internal servers that aren’t even routable because they don’t have public addresses. I hope non-routable servers will become less common in an IPv6 world!
If you get your SSH client configured correctly then it feels just like a VPN. You can do port-forwarding and even do DNS lookups in the remote network (that is, using the Route53 zones attached internally to the VPCs).
If you are using a Windows machine then I recommend using Putty and specifying your jump box under Connection > Proxy in the GUI.
Let’s say that your VPC has the internal address range 172.21.0.0/16 and your bastion host is bastion.com . Your config under Connection > Proxy in the GUI will be something like:
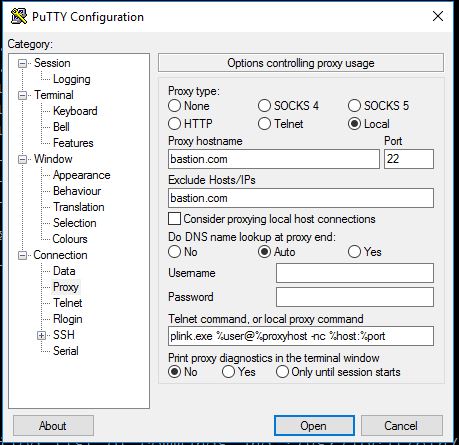
You will need to have putty.exe and plink.exe in your PATH (possibly in the same folder?) then you can just open Command Prompt and run putty 172.21.12.34 or putty server01.local and it will connect to the server via the jump box.
If you would like to copy-and-paste the incantation then here it is:
plink.exe %user@%proxyhost -nc %host:%port
(Thanks to Martin Prikryl on StackOverflow: https://stackoverflow.com/questions/28926612/putty-configuration-equivalent-to-openssh-proxycommand)
Oh and don’t forget to add bastion.com to the ‘Exclude Hosts/IPs’ otherwise Putty will go into an infinite loop until your computer crashes!
The magic plink.exe command very similar to how you would configure OpenSSH. If you’re on a Mac or Linux machine then you can use the ProxyCommand feature by adding the following to your ~/.ssh/config file:
Host 172.21.*.* ProxyCommand ssh -q -W %h:%p bastion.com
In the past I have also had some success with a technique called ‘agent forwarding’ but I decided to switch to using the ProxyCommand directive after reading this article: SSH Agent Forwarding considered harmful.
That’s it! Please leave a note below if you found this helpful or have any other comments.